Configure Authorization Extension
Before the extension can enforce your authorization logic, you need to configure how it will behave during the login transaction. Your configuration settings will be captured in a rule that executes during runtime.
Prerequisites
Install the Authorization Extension
Configure extension
Go to Auth0 Dashboard > Extensions, and select Auth0 Authorization.
Choose Configuration at the top right of the Authorization Dashboard.
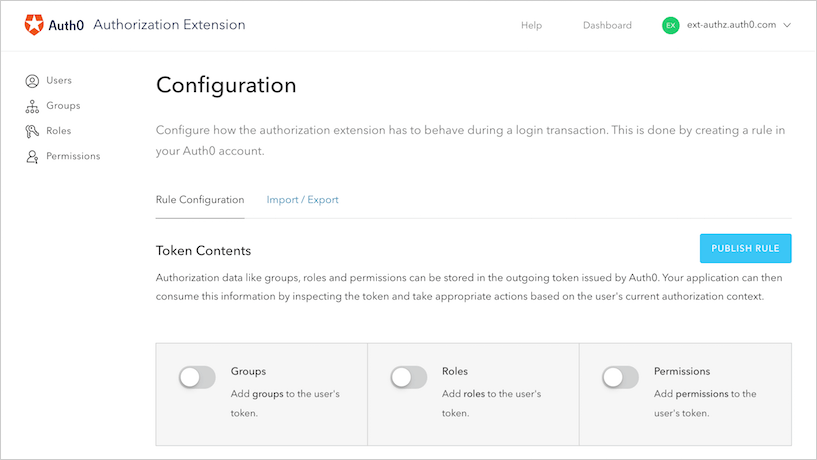
This brings you to the Rule Configuration section of the Configuration page. All of the changes you make in the sections under Token Contents, such as those related to groups, roles, and permissions, will be reflected in the rule you export at the completion of this step.
ApiKey
The rule uses the ApiKey to communicate with the Authorization Extension API and get the policy. The ApiKey is stored as a rule config and will be created automatically when the rule is published. To rotate the ApiKey, click the Rotate button; when the ApiKey is rotated, the rule config will be updated automatically.
Add authorization information to the token issued
You can store authorization data like groups, roles, or permissions in the outgoing token issued by Auth0. Your application can then consume this information by inspecting the token and take appropriate actions based on the user's current authorization context.
To add groups, roles, and/or permissions information to the outgoing token, enable the slider next to the option you want to be included.
Merge authorization data from IdP
You might have users that receive groups, roles, or permissions from the identity provider (IdP) you're using, such as Active Directory. If you want to merge these items (to preserve them) with the ones defined in the Authorization Extension, make sure you enable the appropriate Passthrough options. Enable the slider next to the appropriate merges you want enabled.
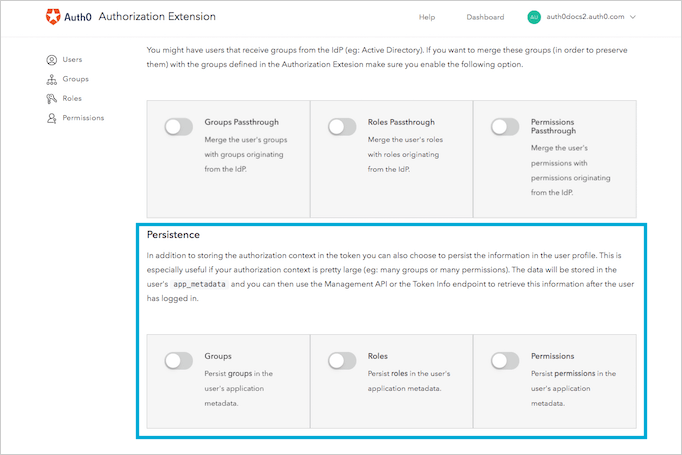
Store authorization information in user profiles
If your authorization context is large (for example, the user might belong to many groups or have been granted many permissions), you might find it useful to store some of the authorization content in the users' profiles. This allows you to store less information in the token, which means you're less likely to see performance-related issues or even problems with token issuance. Persistence is the process by which you store groups, roles, and permissions information in the users' profiles.
The data will be stored in the user's app_metadata field, and you can then use the Management API or the Dashboard to retrieve this information after the user has logged in.
Save changes to rule
Once you've configured your rule, click Publish Rule. This creates a rule for your tenant that executes after each user login.
View rule
If you'd like to see the rule you've created, you can do so at Auth0 Dashboard > Auth Pipeline > Rules.
You can open the rule to see the exact rules configuration.

